SAML 2.0 SSO
Lyyti supports the SAML 2.0 protocol for Single Sign-On. It enables the Service Provider ("SP", ie. Lyyti) and Identity Provider ("IdP", whatever you use for managing logins) to share their authentication and authorization data using standardized XML metadata.
Configuration
- SAML 2.0 SP metadata as XML: <https://www.lyyti.fi/access/saml2/metadata/YOUR_ID_HERE>
- Entity ID: <https://www.lyyti.fi/>
- ACS: <https://www.lyyti.fi/access/saml2/acs/YOUR_ID_HERE>
- URL to initiate SSO: <https://www.lyyti.fi/access/saml2/sso/YOUR_ID_HERE>
- The only Name ID (ie. what is used to identify the account attempting login) needed is the user's email address
- Sign responses, but not requests
- Note: The email provided by your IdP as the user's NameID must match the user's Lyyti account email
Once you have entered these SP settings and the XML metadata into your SAML 2.0 configuration, please provide us the IdP metadata in XML format. The SSO and ACS URLs provided above will become functional only after we have received and processed the metadata.
Example
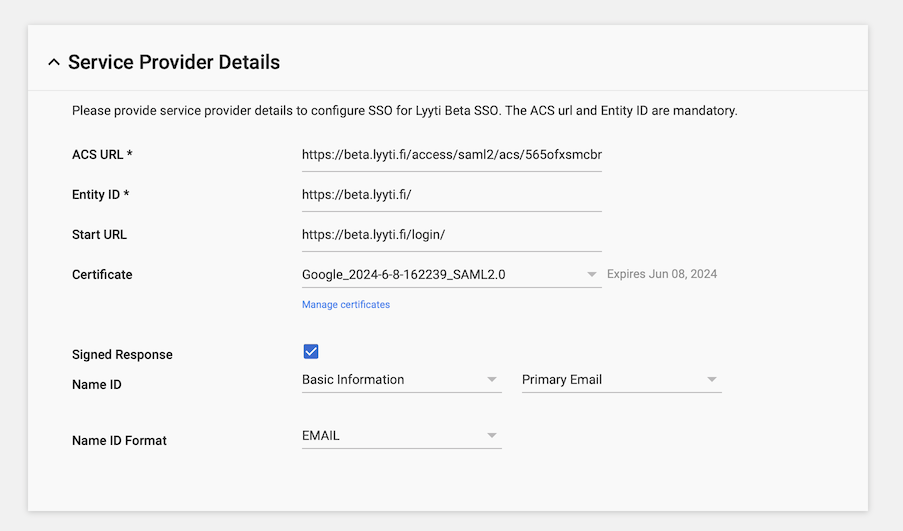
Example of the SAML 2.0 SP settings panel when using Google as the IdP
Available settings
The only currently available Lyyti-specific setting regarding SSO is the decision whether or not to allow SSO discovery by user email. What this means is that in order for the Lyyti login page (<https://portal.lyyti.fi/login/>) to work, it needs to know the SSO URL of the user attempting to log in.
Because this happens, by definition, before the user has logged in, the discovery process is "public" in that anyone could theoretically test different user emails to find out a) that such an account exists and b) what kind of SSO they use to log in. This may or may not be a significant detail for your organization's cybersecurity strategy. A common practice these days seems to be to enable public discovery, but Lyyti supports both options.
If you choose to disallow SSO discovery by email, then the Lyyti login page will not work for your organization's users, and you must direct the users to the organization-specific SSO URL provided above. By default, we will not turn discovery by email on, so please inform us if you decide to allow it.
Updated 9 months ago
